Advanced topics
Advanced topics
Here will be discussed more complex use cases.
JavaScript auth
This kind of flow, must be used only if there is no possibility to authorize user using server flow. In this
case id_token will be added to resulting uri, so it can be fetched using Javascript.
This flow can be enabled while setting response_type to id_token like in example:
https://oauth2-cl.dizme.io/v2.0/oauth2/auth?
response_type=id_token&
client_id=2a9ead06-f829-43ea-9e8e-39bc62be3b00&
scope=openid&
redirect_uri=https://example.com/oauth_back_dizme/&
state=5RP7TK9lgvZPSti&
nonce=8rYBFeJpYMVx6DY
User, once completed flow, will be redirected on redirect_uri with additional parameters:
http://example.com/oauth_back_dizme/?status=ok&code=<code>&id_token=<jwt_token>&scope=openid
Use well known paths to validate jwt token.
The Discovery document
The OpenID Connect protocol requires the use of multiple endpoints for authenticating users, and for requesting resources including tokens, user information, and public keys.
To simplify implementations and increase flexibility, OpenID Connect allows the use of a "Discovery document," a JSON document found at a well-known location containing key-value pairs which provide details about the OpenID Connect provider's configuration, including the URIs of the authorization, token, revocation, userinfo, and public-keys endpoints. The Discovery document for RP's OpenID Connect service may be retrieved from:
https://oauth2-cl.dizme.io/.well-known/openid-configuration
Output is the Json document:
{
"issuer": "https://oauth2-cl.dizme.io",
"authorization_endpoint": "https://oauth2-cl.dizme.io/v2.0/oauth2/auth",
"token_endpoint": "https://oauth2-cl.dizme.io/v2.0/oauth2/token",
"userinfo_endpoint": "https://oauth2-cl.dizme.io/v2.0/oauth2/userinfo",
"jwks_uri": "https://oauth2-cl.dizme.io/v2.0/oauth2/certs",
"response_types_supported": [
"code",
"id_token"
],
"subject_types_supported": [
"public"
],
"id_token_signing_alg_values_supported": [
"RS256"
],
"scopes_supported": [
"openid"
],
"token_endpoint_auth_methods_supported": [
"client_secret_basic",
"client_secret_post"
],
"claims_supported": [
"aud",
"email",
"email_verified",
"exp",
"iat",
"iss",
"jti",
"nickname",
"name",
"picture",
"sub"
],
"grant_types_supported": [
"authorization_code"
]
}
Appendix
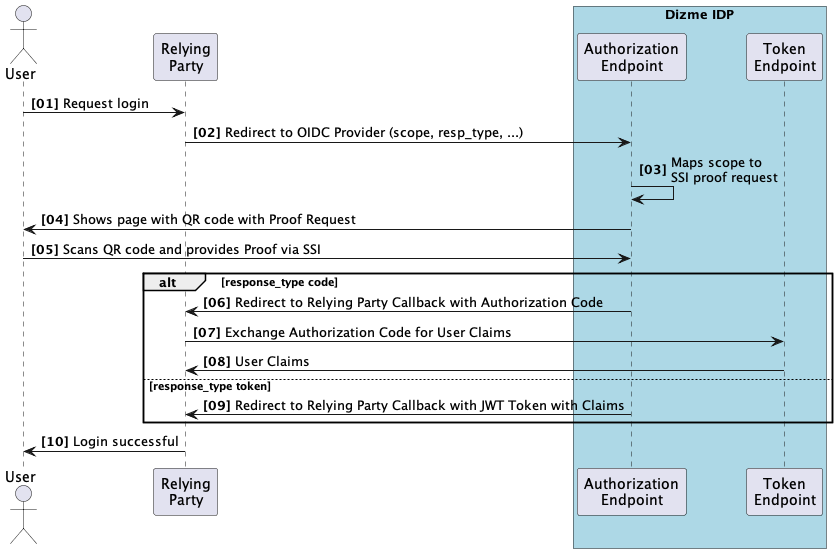
Sequence